A recently discovered vulnerability within Mac’s Keychain has left Mac users at risk. Find out how you can take steps to protect your personal information and yourself from becoming exposed.
Technology is supposed to make our lives easier, and Apple engineers designed the Mac Keychain to do just that. Designed to store, encrypt, and only discerningly release login credentials, credit card numbers, and other sensitive information to user-authorized applications, Keychain is supposed to be a safe way to free yourself from the headache of remembering hundreds of different passwords and login names, sort of like a high-tech vault.
Keychain Vulnerability
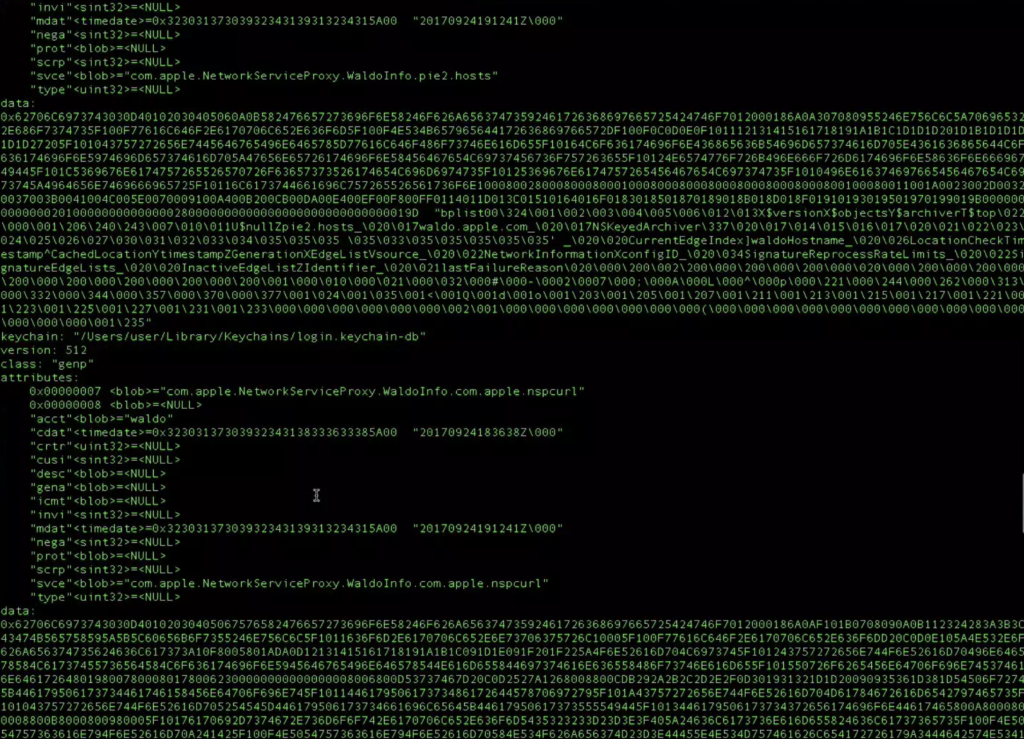
On September 25, 2017, however, former National Security Agency (NSA) staff member Patrick Wardle Tweeted a video in which he demonstrated his discovery of a major vulnerability in Keychain. This vulnerability puts all Mac users at risk. In this video, Wardle shows how a malicious application downloaded onto a computer can infiltrate Keychain, dump its encrypted passwords, and translate them into plain text. With this information, a criminal could simply sign into not only your social media accounts but your bank accounts, too.
In this video, Wardle uses an unsigned application, meaning the application is not signed with code from a trusted source, to remove the personal information from Keychain. Apple software is designed to prevent users from downloading unsigned applications, but almost anyone can create a signed application by paying a small annual fee to sell through Apple’s App Store. Wardle later posted a list of clarifications and further information on Patreon which specifically states that either a signed or an unsigned malicious application could pilfer anyone’s information. He clarified his use of an unsigned application was intended to emphasize the degree of the weakness within Keychain.
Although they surely will, Apple has yet to release a software update to fix the issue. In the meantime, here is what you need to know about this vulnerability in order to protect your passwords and any other personal information you have stored in Keychain (bank account PINs, credit card numbers, super secret family recipes, etc.).
Sierra, High Sierra, and Probably El Capitan Affected
Although Wardle has only tested the Keychain vulnerability on the Sierra and High Sierra operating systems, he is confident that El Capitan and any other older Mac operating systems currently running Keychain would also be at risk. Contrary to what some sources have reported, the vulnerability is not solely with High Sierra. Mac users who have not yet updated their operating systems to High Sierra should not delay doing so due to the recent discovery of this vulnerability in Keychain.
Older operating systems quickly become outdated with the release of new software and likely expose users to a plethora of additional risks. Keeping your software and operating systems up to date by always downloading the latest patches and update releases is the best way to protect yourself and the private information on your computer from becoming public.
Not All Keychain Users Have Been Exposed
Mac Keychain users do not need to panic just yet. Wardle has not disclosed specifically how the vulnerability works – except to the software engineers at Apple – and the vulnerability does not automatically expose all Mac Keychain users. In order for Keychain to release passwords and other personal information stored within its confines, the Mac user must first download a malicious application designed to pilfer information out of Keychain onto his or her computer.
In other words, in order for criminals to leverage this vulnerability, they have to be able to convince computer owners to download their malicious applications. These downloads could come in the form of phishing email scams with dangerous links or attachments, pop-ups encouraging you to download fake software updates, or through downloads from un-trusted or unknown sources.
Mac Users: How to Protect Your Personal Information Prior to a Software Update
Engineers at Apple are already working to provide Mac users a security patch update to fix the Keychain vulnerability. A solution, however, likely will not happen overnight. In the meantime, Mac users can take steps to protect their personal information from becoming exposed by continuing to follow the cybersecurity safety precautions they likely already know, such as:
- Not opening attachments or clicking on links sent from unknown sources
- Not opening unexpected attachments or links sent from known sources
- Only downloading software from trusted websites
- Regularly updating your software and operating system
- Only updating software from within the applications themselves or through the App Store
Following this advice will prevent you from falling prey to phishing scams which could lead you to unintentionally downloading malicious, password-pilfering software onto your computer.
Additional Security Support from Bralin Technology Solutions
If you are ever uncertain about whether an update or download is legitimate or if you suspect your electronically stored personal information might have been compromised through the Mac Keychain vulnerability or through another channel, we encourage you to seek advice from an IT expert. At Bralin Technology Solutions, we can help you establish a solid set of security credentials and ensure your software is always up to date. For more information regarding Mac Keychain, its vulnerability, and how to safeguard your passwords, contact a Bralin Technology Solutions IT professional in North Battleford & Lloydminster by calling (306) 445-4881 or (306) 825-3881 or emailing info@bralin.com.
We look forward to helping you keep your private information from going public.







 Lloydminster
Lloydminster